In today’s digital landscape, smartphones are not just communication tools; they are extensions of our lives, housing personal, sensitive information. With this in mind, the risk of theft cannot be overstated, making effective stolen device protection a priority for users. Both Apple and Samsung recognize the need for advanced security measures and have embraced this challenge with an array of features designed to safeguard their devices. By examining and comparing these security options, users can gain a better understanding of which brand best suits their individual needs. This exploration delves into the intricate nuances of how Apple and Samsung protect their users from the repercussions of device theft.
Choosing between Apple and Samsung when considering smartphone security can be daunting. Each brand offers distinctive features that cater to different preferences and requirements. Apple leans heavily on its robust privacy policies and intuitive interfaces, creating a seamless experience for users. Conversely, Samsung provides a more layered approach to security, appealing to those who might be looking for advanced functionalities and enterprise-level protections. As we delve deeper into this topic, it’s essential to keep in mind that the ultimate goal is to not only protect the device but also to ensure peace of mind for users.
Overview of Stolen Device Protection

Apple and Samsung each boast a range of features designed specifically to protect users from theft. Understanding these capabilities can make it easier for consumers to navigate their options effectively. Below is a brief overview of some essential features offered by both companies:
- Real-time location tracking – Both companies provide services that help locate lost or stolen devices.
- Remote lock and erase options – Users can secure their data by locking or wiping their devices remotely.
- Provider-specific privacy enhancements – Features unique to each platform that enhance user privacy.
Apple Device Protection Features

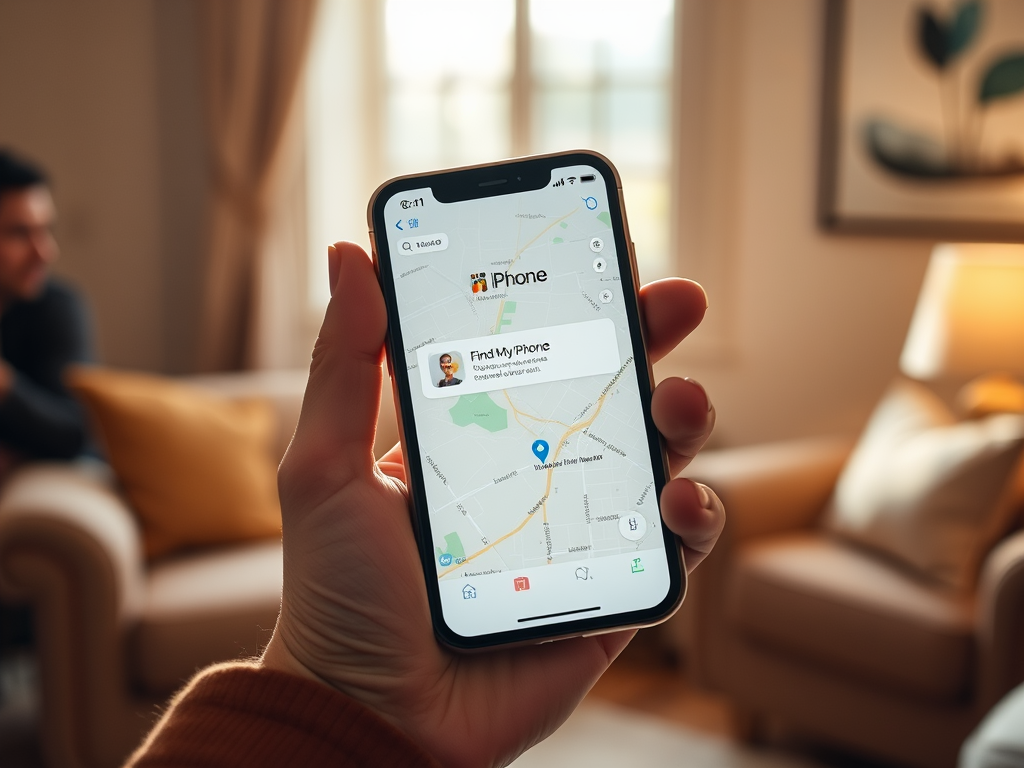
Find My iPhone
Apple’s “Find My iPhone” is a cornerstone of its device protection strategy. This feature allows users to track their lost devices in real-time, giving them a powerful tool against theft. Users simply access the service via their iCloud account or find the app on another Apple device. Once activated, it displays the device’s location on a map. The ease of use is also an important part of its appeal, making it accessible to all users, regardless of technical proficiency. In emergencies, the option to lock or erase data further empowers users, ensuring their information remains secure.
Activation Lock
Alongside Find My iPhone, Activation Lock plays a crucial role in Apple’s security framework. It acts as an additional barrier by binding the device to the owner’s Apple ID. If an unauthorized person attempts to use the device, they’ll encounter a formidable wall requiring the original owner’s credentials. This feature is just another layer bolstering security, making it significantly harder for thieves to profit from stolen devices. Users are equipped with alerts if the device is being activated without their knowledge, thereby increasing vigilance. In this way, Activation Lock stands as a testament to Apple’s commitment to user security.
Privacy and Encryption
Apple champions user privacy, which is reflected in its encryption practices. Data on Apple devices is encrypted by default, protecting it from unauthorized access. Further, the implementation of two-factor authentication is a vital feature that requires a second form of verification before access is granted. This multi-layered approach is significant in today’s climate of data breaches and cyber threats. Users benefit from knowing both their data and their identities are protected against intrusions. As a result, Apple continues to enhance security features to keep up with evolving threats.
Samsung Device Protection Features
Find My Mobile
Samsung’s “Find My Mobile” service competes directly with Apple’s offerings. It empowers users to locate their devices, similar to Apple’s feature, but also includes options for remote unlocking. This can be particularly advantageous if a user has forgotten their password or has accidentally locked themselves out. Users can also back up specific data before recovering the device, keeping vital information intact. This flexibility provides users with choices, allowing them to determine what matters most during a stressful situation. It is important to note that this range of capabilities enhances usability while still prioritizing security.
Samsung Knox
Samsung Knox represents a multi-layered security solution that protects both hardware and software from various threats. It ensures that even if a device is lost, the sensitive data within it can remain inaccessible to anyone else. Knox sends real-time alerts in case of unauthorized access attempts, which can be crucial in preventing data breaches before they occur. Additionally, businesses benefit significantly from Knox, as it complies with stringent regulations, offering a secure environment for enterprise users. This feature underlines Samsung’s commitment to comprehensive security, making it an ideal choice for corporate settings. Users confident in Knox will feel a renewed layer of security surrounding their vital information.
Privacy Features
Samsung’s devices come with robust features that further enhance privacy. One noteworthy capability is the “Secure Folder,” an encrypted space on the device for storing sensitive data away from prying eyes. Users can place documents, photos, and even apps into this secure area, ensuring that even if the device is lost, certain data remains protected. Furthermore, Samsung employs biometric security measures including fingerprint and facial recognition to provide easy yet secure access. This biometric layer adds a modern touch, aligning with today’s mobile security standards. Ultimately, Samsung’s privacy features can significantly enhance user trust and confidence in their device’s security.
Key Comparisons
When it comes to comparing the stolen device protection features of Apple and Samsung, several vital factors emerge:
| Feature | Apple | Samsung |
|---|---|---|
| Real-time Tracking | Find My iPhone | Find My Mobile |
| Remote Actions | Lock, Erase, Sound | Unlock, Backup |
| Security Protocols | Activation Lock, Encryption | Knox Security |
| User Alerts for Unauthorized Access | Device Notifications | Real-time Alerts |
Conclusion
Both Apple and Samsung have made significant strides in protecting stolen devices, each offering a unique approach to security. While Apple’s focus on privacy and user-friendly features caters well to general consumers, Samsung’s advanced tools, particularly for business users, provide a comprehensive security framework. Ultimately, the choice between Apple and Samsung may come down to individual security preferences and usability needs. The landscape of smartphone security is ever-evolving, and both companies are continuously innovating to stay ahead of potential threats. Users should weigh the features that matter most in their daily lives and make informed decisions to safeguard their digital treasures.
Frequently Asked Questions
- What should I do if my Apple device is stolen? Use Find My iPhone to locate, lock, or erase your device remotely.
- Can I track my Samsung device if it is turned off? You may not be able to track a powered-off device, but you can view its last known location through Find My Mobile.
- Do both devices offer two-factor authentication? Yes, both Apple and Samsung provide two-factor authentication as an extra layer of security.
- Is Samsung Knox available on all Samsung devices? Knox is available on most mid-range and high-end Samsung devices, but not on all models.
- How does Activation Lock work for Apple devices? Activation Lock ensures that only the owner can reactivate the device using their Apple ID credentials if it’s lost or stolen.